Automating FTP Virus Scans with Kaspersky Antivirus - Part 3

In Part 1 of this article, you learned how to perform a basic automatic Kaspersky scan on a newly uploaded file. In that post, we only specified one argument for the kav4fs-control command, and that was the path of the file to scan.
In most instances, however, you may also want to specify a specific action for Kaspersky to take in the event that the uploaded file is found or suspected to be infected by malware. For example, you might want to quarantine the file in question. For our final installment of this article, we'll not only show you how to send an infected file to quarantine, we'll also show you how to configure your managed file transfer server to email you a notification whenever such an event happens.
How to receive notification when an infected file is quarantined
First, you need to modify the Kaspersky Virus Scan Trigger you created in Part 1. Launch your JSCAPE MFT Server Manager, open your domain, and click the Triggers node. Next, select the Kaspersky Virus Scan trigger (or whatever name you assigned to that trigger) and click the Edit button.
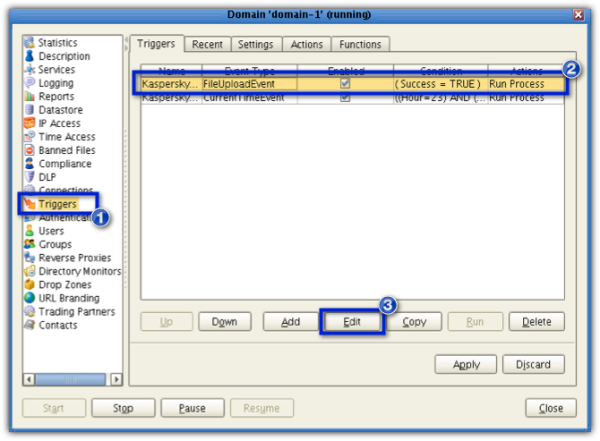
When the Edit [name of trigger] Trigger(Step 1 of 3) screen appears, click Next.
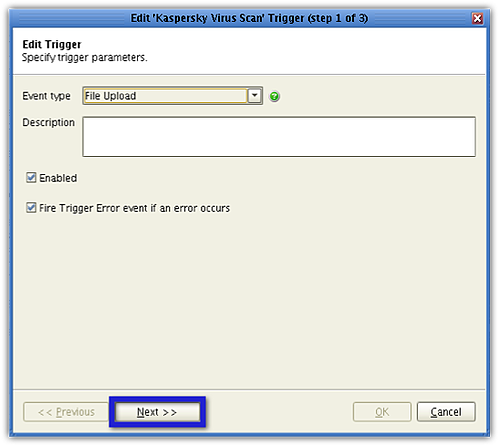
Click the Next button again in the succeeding screen.
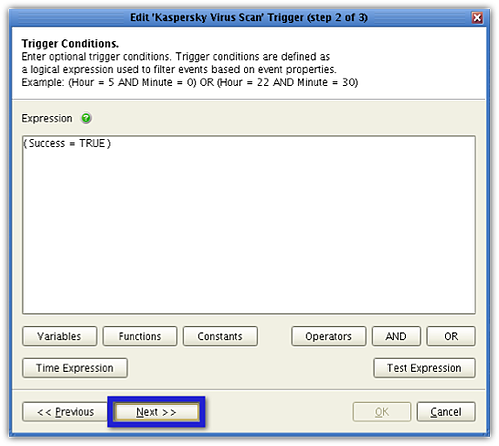
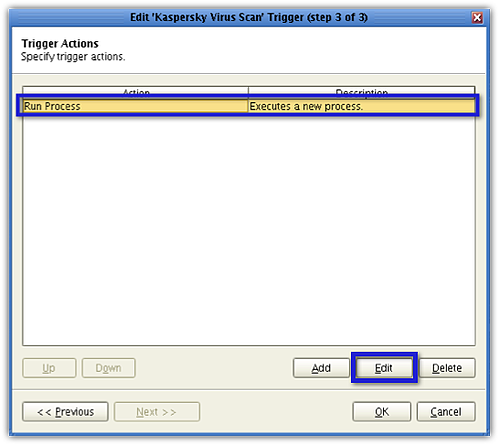
In Step 3 of the Wizard (the Trigger Actions screen), select the Run Process action and then click the Edit button.
In the Edit Action screen, go to the Arguments field and insert the following argument:
--action Quarantine
So the contents of the Arguments field will now look like this:
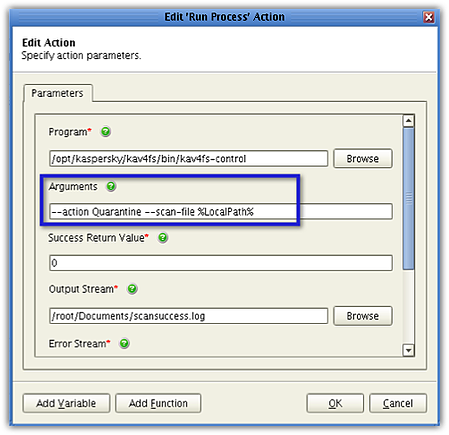
Click OK. And then click OK again when you're back in the Trigger Actions screen (window step 3 of 3).
Once you're back at the main screen, click the Apply button.
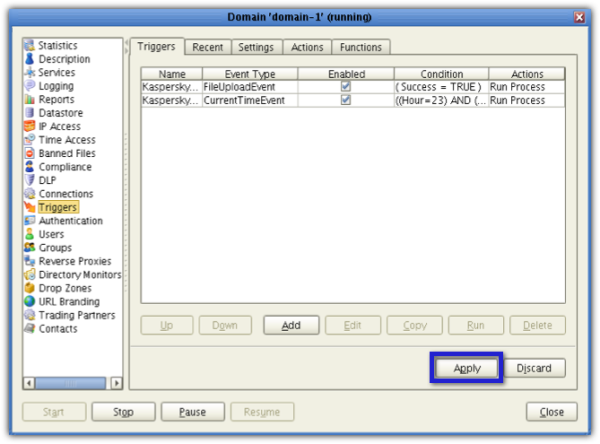
So now, every time a newly uploaded file is found to be infected with malware, the file will be sent to Quarantine. By default, the designated quarantine folder of Kaspersky Antivirus 8 for Linux File Server is:
/var/opt/kaspersky/kav4fs/quarantine
To receive an email from JSCAPE MFT Server notifying you of a recently quarantined file, which would of course mean an infected file has been recently uploaded to your server, you first create a Directory Monitor for that quarantine folder. This can then be used in conjunction with a trigger whose corresponding Trigger Action would be to send you an email.
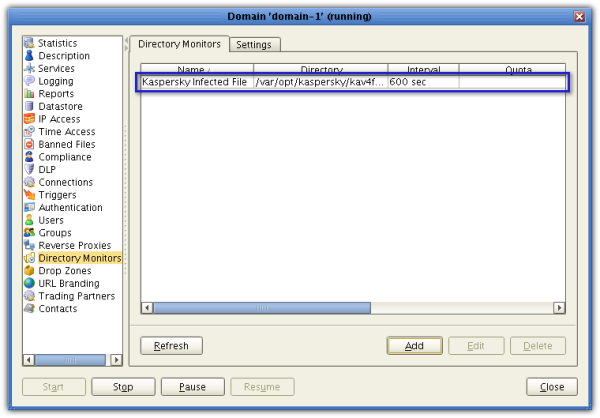
Let's proceed by creating that Directory Monitor. Go to the Directory Monitor node and click the Add button.
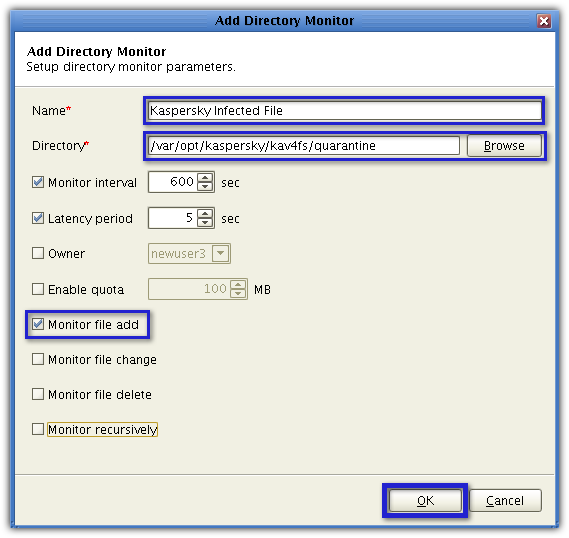
Give your directory monitor a name (e.g. Kaspersky Infected File).
Next, click the Browse button and navigate to the Kaspersky quarantine folder (/var/opt/kaspersky/kav4fs/quarantine). Make sure the Monitor file add checkbox is checked. You may uncheck the succeeding checkboxes for now. When you're done, click OK.
You should then see you're newly created directory monitor among the list of directory monitors.
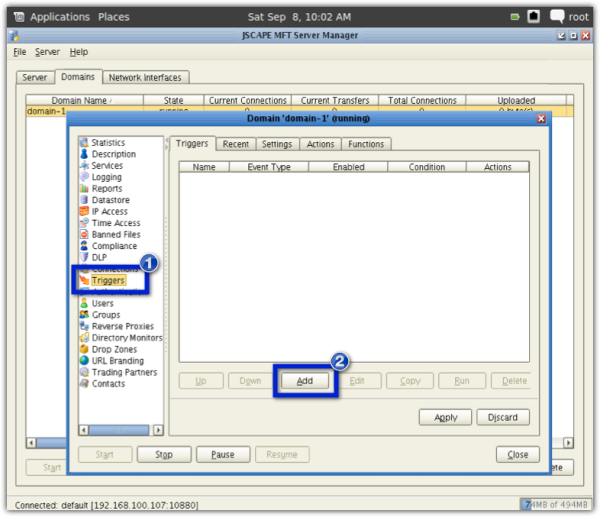
Now for the last step. We need to add a trigger that would send an email each time a new file is added to the quarantine folder. Go to the Triggers node and add a new trigger now.
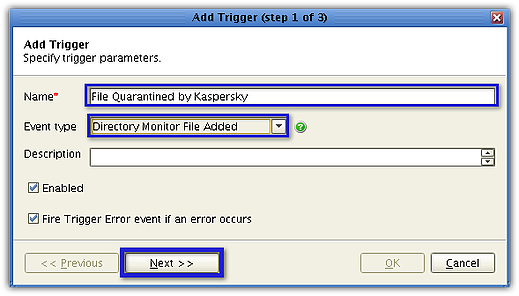
Give the trigger a name (e.g. File Quarantined by Kaspersky). From the Event Type drop-down list, select Directory Monitor File Added. When you're done, click Next.
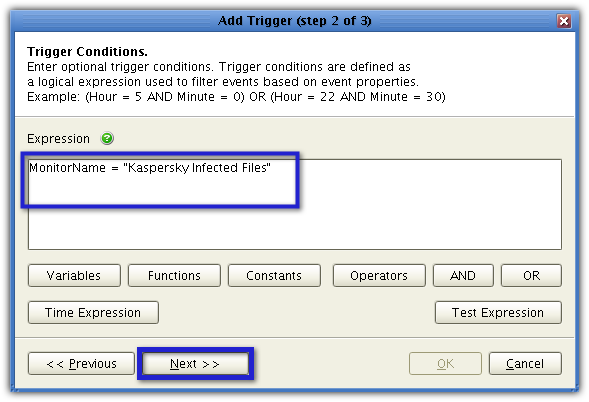
In the Expression box, enter:
MonitorName = "Kaspersky Infected Files"
wherein "Kaspersky Infected Files" is assumed to be the name you assigned to the directory monitor. If you assigned a different name, use that. Click Next.
Click the Add button to add a new trigger action.
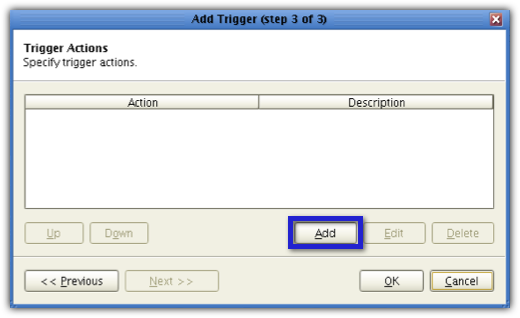
From the Action drop-down list, select Send Email and then click OK.
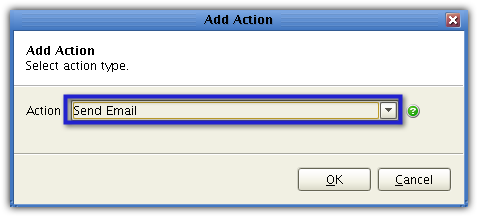
Enter information pertinent to the sender's email account like the Hostname, Port, Connection Type, username, password, subject, body. The values you enter into the Hostname, Port, and Connection Type will depend on the email hosting service. What you see here is for Gmail. Enter the sender's email into the Fromfield and the recipient's email into theTofield.
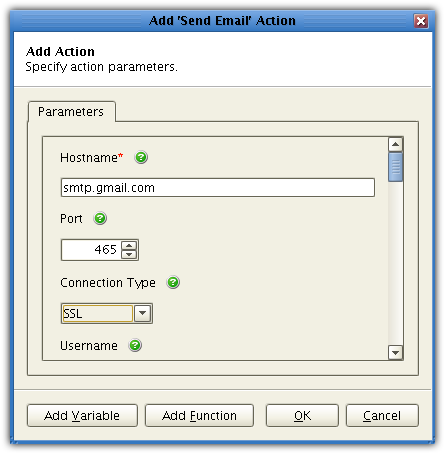
Once you see the newly created trigger action in the list of trigger actions, click OK.
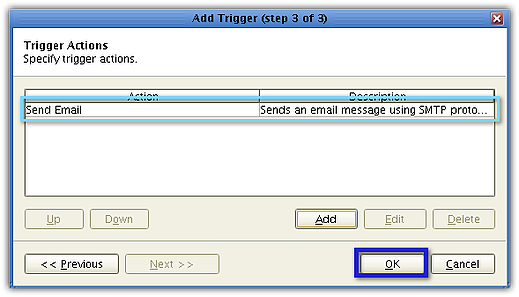
You should then see your newly created trigger inside your list of triggers. Click Apply.
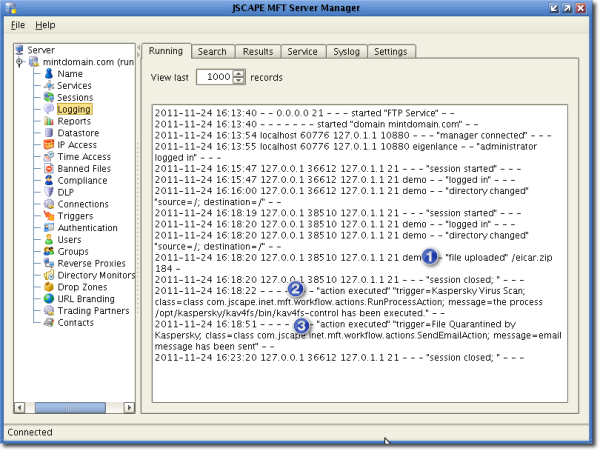
To see how our system would react if an actual infected file would be uploaded, we tried a test virus file provided by Kaspersky named eicar.zip. Note, this file is not an actual virus but will be treated by Kaspersky as if it were. Here's how our JSCAPE MFT Server Manager Logging screen looked like right after these three events:
1. The file was uploaded;
2. The trigger action for scanning a newly uploaded file was executed; and
3. The trigger action for sending a notification email, following a quarantine process, was executed.
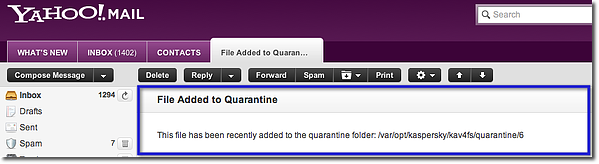
And here's the corresponding screenshot of the actual email, viewed from the recepient's screen.
That wraps up our 3-part article on an automated FTP virus scan using Kaspersky and JSCAPE MFT Server. I hope you learned a lot. See you again next time.
Summary
In this post, you learned how to enhance your secure file tansfers by configuring JSCAPE MFT Server to: perform automatic Kaspersky-powered virus scanning on uploaded files, auto-update the Kaspersky database, and send email notifications as soon as an infected file is quarantined.