What Is An SFTP Key?

What is an SFTP key?
Used at the start of a Secure File Transfer Protocol (SFTP) session, an SFTP key is a type of credential you load on an SFTP client to authenticate with an SFTP server. SFTP keys are commonly used in automated SFTP file transfers, but you can also use them in user-initiated file transfers, either on their own or alongside a password for two-factor authentication (2FA).
If you want to maximize the potential of your SFTP solution and make sure it’s only accepting SFTP connection requests from legitimate users and client applications, you’ll want to know what SFTP keys are, how they work and how to use them properly.
The role of SFTP keys in SFTP public key authentication
SFTP keys are used in SFTP public key authentication. It’s an authentication method based on public key cryptography, a cryptographic process that involves two mathematically linked keys — a private key and a public key. A private key can only work with the public key that matches it and vice versa. In case you’re wondering what these “keys” look like, they’re actually strings of characters similar to the ones shown below.
Here’s how a typical private key looks like. This sample key is encoded in a format known as Rivest-Shamir-Adleman (RSA):
-----BEGIN RSA PRIVATE KEY-----
MIIEpAIBAAKCAQEAzZm9vZGJhcgLW1LqBkQJ4kqlE77VrYQuCw5+/6y+V3JYI8G
3o7S9y9kGwtMJdSozZ43xZkEhKq+oOdgR/tKbztb5/zVz0Qs3/6EpbhTsTgVbfmI0
8bHQyl7vZpPNSuyy4Qvz1fw+YsQ2W2C/PEpmlo3zSihq6ZIX1e8ciWu5w+V0WY6A
6p3jL87fUF+Uo/3GpV8qQ4FZrN6Y0gSgmmOYmzOU8rTcZ7XirHcONJ3p/WGwssHS
1q78cOhe1I7l5v8MzLWKcl/zozirJln2v2Zf7EaHXXJiMfgXvb5z2xSHkNp7BCO1
qVMZWuRiGrUtzJscWdURi12t/tyiXc+hFuY+tQIDAQABAoIBAHxP1xLw9THM9eh6
rdDuvNHzvMvevjt2NzesU6Puh3R8i6ZiX5EUGfOi5sECgYEA1xGJDBro1V4KJ5k2
DDKkXlzDxKWDCs16rrohY0fzPQwZoij+kwXueGQbj4djrFrLLv7//Tz6CSsQlroO
hd1nuh3pl/MaBZ5XZL+0f0kF5l6O7v9sVFKYRcAlh9QYLqyUuShTC3ZUNFAEwVOV
...
-----END RSA PRIVATE KEY-----
Here’s that private key’s corresponding public key, also encoded in RSA format:
-----BEGIN RSA PUBLIC KEY-----
MIIBCgKCAQEAzZm9vZGJhcgLW1LqBkQJ4kqlE77VrYQuCw5+/6y+V3JYI8G3o7S
9y9kGwtMJdSozZ43xZkEhKq+oOdgR/tKbztb5/zVz0Qs3/6EpbhTsTgVbfmI08bHQ
yl7vZpPNSuyy4Qvz1fw+YsQ2W2C/PEpmlo3zSihq6ZIX1e8ciWu5w+V0WY6A6p3j
L87fUF+Uo/3GpV8qQ4FZrN6Y0gSgmmOYmzOU8rTcZ7XirHcONJ3p/WGwssHS1q78
cOhe1I7l5v8MzLWKcl/zozirJln2v2Zf7EaHXXJiMfgXvb5z2xSHkNp7BCO1qVMZ
WuRiGrUtzJscWdURi12t/tyiXc+hFuY+tQIDAQAB
-----END RSA PUBLIC KEY-----
Public key cryptography is employed in various cryptographic operations, not just authentication.
For instance, you can use it in encryption and decryption, where the public key is used as an encryption key, while the private key is used as a decryption key. Since the two keys work in pairs, only a public key’s matching private key can decrypt files encrypted by that specific public key. This prevents users or applications from decrypting files using an invalid private key.
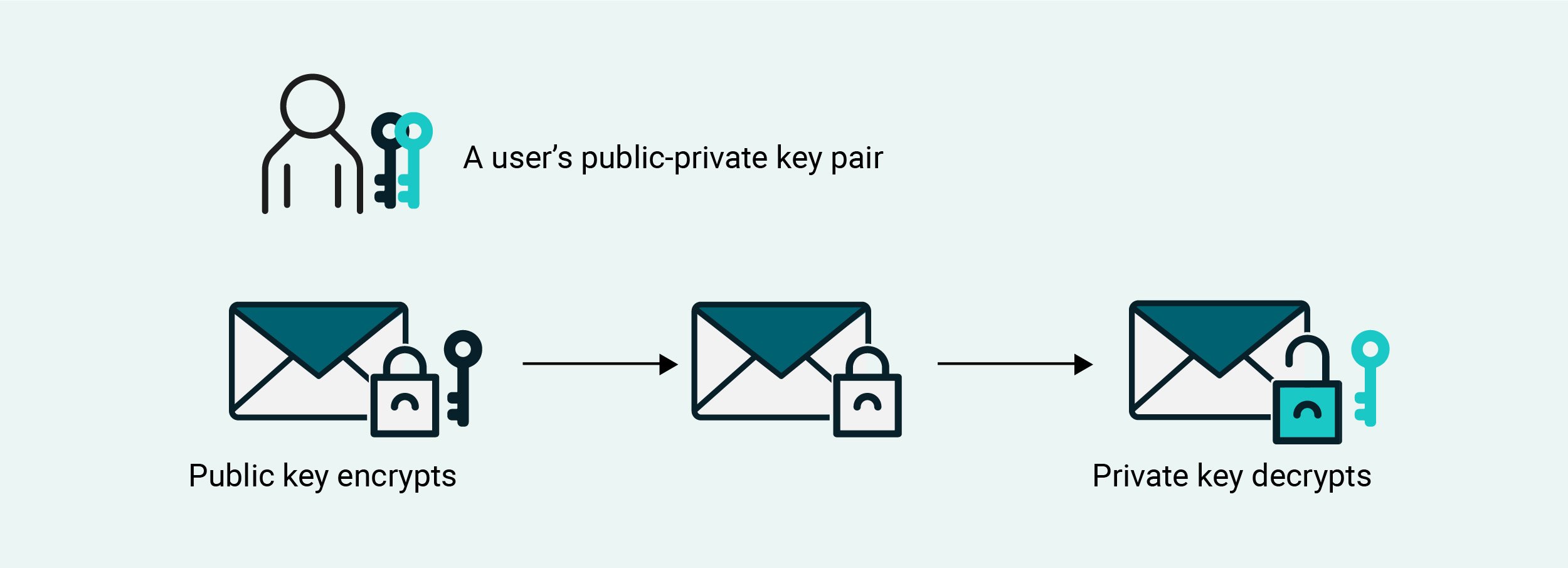
Public key cryptography can also be used in digital signing and verification. The private key is used to generate a digital signature and the public key is used to verify the authenticity of that signature. Again, since the two keys work in pairs, a digital signature generated by a non-matching private key will fail a public key’s verification process.
Public key authentication takes signing and verification a step further. In the case of SFTP public key authentication, you store a public key in your SFTP server, link that public key to a user account and then have the owner of that user account save the corresponding private key. When used in this context, this private key is often called an SFTP key.
When the owner of that user account connects to your server via an SFTP client, the client submits a digital signature generated by the private key, a.k.a. SFTP key. In turn, your server uses the public key to verify the signature. If the verification process succeeds, it means the digital signature was sent by a user or client in possession of a matching private key. As a result, the user or client is deemed authenticated.

Note: Technically speaking, the SFTP public key authentication process we just described is for authenticating clients. You can also use SFTP public key authentication to authenticate servers. If you want to know more about SFTP server authentication and host key fingerprints, read the article, “The SSH/SFTP key fingerprint and its role in server authentication”
SFTP keys vs. SSH keys vs private keys — What’s the difference?
In many articles, including this one, the terms “SFTP key”, “SSH key” and “private key” are sometimes used interchangeably. While these terms do sometimes mean the same thing, it’s not always the case. You also have to consider the context in which those terms are used.
SFTP keys are indeed private keys, but not all private keys are SFTP keys. For example, Pretty Good Privacy (PGP) also uses public/private key pairs. However, PGP private keys aren’t considered SFTP keys. A private key is only considered an SFTP key when it belongs to a public/private key pair used in SFTP public key authentication.
SFTP keys can also be considered SSH keys. That’s because SFTP obtains its security functions from Secure Shell (SSH). So, the keys used in SFTP are considered SSH keys. That being said, SSH keys can mean either SFTP private keys or public keys.
How to create SFTP keys in 3 different scenarios
Now that you know what SFTP keys are and how they work, it’s time for you to learn how to create them.
When using the OpenSSH ssh-keygen command-line tool
In the past, SFTP keys were usually created in the terminal or command-line. We already gave a detailed discussion on the topic in the article “How to setup SFTP public key authentication on the command line”, so I suggest you read that if you want to know more about it. Otherwise, here are the key points of that article.
- SFTP keys are usually created using OpenSSH, an open-source implementation of SSH found in major operating systems, including most Linux distributions, UNIX, macOS and even newer versions of Windows Server.
- You can create a public/private key pair using the OpenSSH ssh-keygen utility tool. Once created, the private key is typically saved in a file named id_rsa, and the public key in a file named id_rsa.pub. During the creation process, you may specify a passphrase, which is used to ensure only the owner of the private key file can use it.
- You would save the private key a.k.a. SFTP key in your local directory and upload its corresponding public key to your remote SFTP server. You would store that public key in a file named authorized_keys. The authorized_keys file stores all public keys associated with valid user accounts on that server.
When launching a Linux instance on AWS EC2
As mentioned in the previous section, most Linux distributions already have OpenSSH installed by default. The Linux instances provided by AWS EC2 have an OpenSSH installation as well.
When you launch a Linux instance on AWS EC2, you’re given the option to create an SSH key pair or select an existing pair. The SSH public key in that pair is automatically stored on the Linux instance. You can, therefore, use the private key in that pair to authenticate with the SSH server on your Linux instance once that instance is up and running. Since SFTP derives its security functions from SSH, you can also use that same key to initiate an SFTP session.

If you choose to create a new key pair, you’ll be asked to specify a name for your key pair as well as choose the key pair type and private key file format. Choose the RSA key pair type and the PEM file format. The PPK format is for user-initiated sessions that use PuTTY, which we’ll cover later in this post.

After you download the PEM private key file, you need to modify it so that it isn’t publicly viewable. To do that, change your working directory to the directory that contains your downloaded file and then execute the chmod command as shown below. Make sure to replace “forlinuxserver” with the name of your downloaded PEM file.
chmod 400 “forlinuxserver.pem”You can then connect to your Linux instance using that private key by executing the following command:
ssh -i “[filename of pem file]” [Linux EC2 instance username]@[instance public DNS name]Let me share with you what I see when I connect to a Linux instance from a Mac computer for the first time. macOS is based on UNIX and has an OpenSSH client installed by default, so I used that client to connect. My SSH client initially warns me that I’m connecting to an unknown host. I just typed in “yes” to proceed.
% ssh -i "forlinuxserver.pem" ec2-user@ec2-13-250-56-108.ap-southeast-1.compute.amazonaws.comThe authenticity of host 'ec2-13-250-56-108.ap-southeast-1.compute.amazonaws.com (13.250.56.108)' can't be established.ECDSA key fingerprint is SHA256:1A2B3C4D5E6F7G8H9IJKLMNOPQRSTUVWXY.Are you sure you want to continue connecting (yes/no)? yesWarning: Permanently added 'ec2-13-250-56-108.ap-southeast-1.compute.amazonaws.com,13.250.56.108' (ECDSA) to the list of known hosts.__| __|_ )_| ( / Amazon Linux 2 AMI___|\___|___|[ec2-user@ip-172-31-22-47 ~]$
Once you’ve made a successful connection, you can exit that session and connect using SFTP. That PEM file can now serve as your SFTP private key. Here’s what I see on my screen when I connect to my Linux EC2 instance. The sftp prompt you see at the end confirms that I have successfully logged on to the SFTP server on my Linux instance.
% sftp -i "forlinuxserver.pem" ec2-user@ec2-13-250-56-108.ap-southeast-1.compute.amazonaws.comConnected to ec2-13-250-56-108.ap-southeast-1.compute.amazonaws.com.sftp>
When using a GUI-based managed file transfer solution
Creating and using SFTP keys in the command-line is not for everybody. If you prefer an easier way to create and use SFTP keys, you can try JSCAPE MFT Server by Redwood. JSCAPE MFT Server is a managed file transfer (MFT) solution that allows you to set up, deploy and automate SFTP file transfer workflows through a graphical user interface (GUI).
In JSCAPE MFT Server, you can generate SFTP keys using two methods. The first method is suited for server admins, while the other is designed for end users. You can ready about these two methods in the article “Two ways to generate an SFTP private key.”
When using PuTTYgen
PuTTY Key Generator or PuTTYgen is a tool for creating public/private key pairs for SSH. Originally designed for Windows systems, PuTTYgen can now be installed on Mac and Linux machines.
We already have an existing blog post that details the process of generating an SSH key pair using PuTTYgen, importing the public key on JSCAPE MFT Server and connecting to the server via SFTP using WinSCP and the generated private key.
If you’re interested in that method of generating and using an SFTP key, I suggest you read the blog post “Public Key Authentication using PuTTY and WinSCP.” The JSCAPE MFT Server instance used in that post is an older version, so the user interface may be outdated. However, the general steps remain the same.
SFTP keys in two-factor authentication
Modern SFTP servers, like JSCAPE MFT Server, have several security-related advantages over plain FTP servers. One of them is the ability to support two-factor authentication. You can implement 2FA by requiring users to authenticate using both password authentication and public key authentication.

SFTP password authentication on a graphical SFTP client

SFTP public key authentication on the same graphical SFTP client
This will make it more difficult for a hacker to gain unauthorized access. Even if that hacker manages to steal a user’s password, that hacker will still be unable to login without the user’s private key.
The article “What is an SFTP client & how do I use one?” illustrates both methods of authentication with screenshots and diagrams, so you can read that if you want to learn more about these two SFTP authentication options.
SFTP keys in automated SFTP file transfers
Although they can be used in user-initiated file transfers, SFTP keys are more commonly associated with automated file transfers. These are transfers that don’t involve user intervention. IT admins prefer SFTP keys over usernames and passwords in these use cases for a few reasons.
- Passwords are susceptible to a number of attacks, including man-in-the-middle, credential stuffing, social engineering, phishing and so on. SFTP keys aren’t.
- Key files can be accessed through scripts and other automation software.
- Keys don’t require any login screens.
- Even if an attacker manages to develop a way to launch a brute force attack on an SFTP server that uses public key authentication, it’s currently computationally impossible for an attacker to succeed due to the sheer length and complexity of digital signatures.
To use SFTP keys in automated file transfers, you would need to perform the following general steps:
- Generate a public-private key pair and store the private key on your server
- Export the public key
- Import the public key into your trading partner's SFTP server

We’ve published a step-by-step tutorial that illustrates these steps in more detail using the graphical user interface of JSCAPE MFT Server. If you want to review those steps, read the blog post “How to use public key authentication with trading partners.”
Other related posts:
In case you want to follow along, you may request a free trial of JSCAPE MFT Server now.